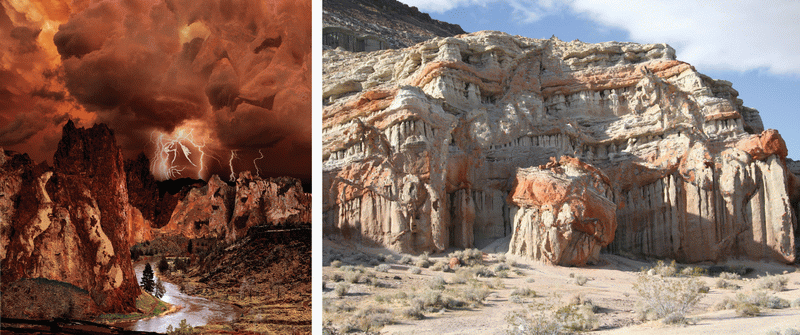

Abstract:
Camouflage images contain one or more hidden figures that remain imperceptible or unnoticed for a while. The ability to delay the perception of the hidden figures is attributed to the theory that human perception works in two main phases: feature search and conjunction search. Effective camouflage images make feature based recognition difficult, and thus force the recognition process to employ conjunction search, which takes considerable effort and time. In this paper, we present a technique for creating camouflage images. To fool the feature search, we remove the original subtle texture details of the hidden figures and replace them by that of the surrounding background. To leave an appropriate degree of clues for the conjunction search, we compute and assign new tones to regions in the embedded figures by performing an optimization between two conflicting terms, namely immersion and standout, corresponding to hiding and leaving clues, respectively. We show a large number of camouflage images generated by our technique, with or without user guidance. We have tested the quality of the images in an extensive user study, showing a good control of the difficulty levels.
Results:
Bibtex:
@article{camouflageImage_sig_10,
author = {Chu, Hung-Kuo and Hsu, Wei-Hsin and Mitra, Niloy J. and Cohen-Or, Daniel and Wong, Tien-Tsin and Lee, Tong-Yee},
title = {Camouflage images},
journal = {ACM Trans. Graph.},
volume = {29},
issue = {4},
year = {2010},
pages = {51:1--51:8},
articleno = {51},
numpages = {8},
}
|
|